Securing the UEFI: A Framework for Memory Forensics in Firmware
In the modern computing landscape, the Unified Extensible Firmware Interface (UEFI) has replaced the older BIOS system, marking a significant step forward in terms of security and functionality.
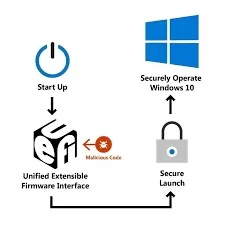
UEFI provides a modular and extensible environment that initializes hardware and loads the operating system, making it a crucial component in modern computing systems. However, as UEFI has become a more integrated part of the system’s boot process, it has also become a prime target for cybercriminals aiming to exploit its persistence mechanisms and control over system execution.
While many advancements in UEFI security mechanisms have been made—such as UEFI Secure Boot and Capsule Updates—these protections are not foolproof. Attackers have found ways to circumvent these defenses, notably through threats like bootkits (e.g., ThunderStrike, CosmicStrand, and Glupteba) that target UEFI during the runtime phase. The lack of specialized forensic tools to analyze volatile UEFI runtime memory remains a major gap in modern cybersecurity, hindering deep analysis of firmware-level threats. In this paper, we introduce a novel framework to address this gap, allowing for effective UEFI memory forensics during the pre-OS phase.
The Challenge of UEFI Threats
Despite the effectiveness of traditional operating system (OS)-level memory forensics, the lack of tools tailored for UEFI analysis is a critical oversight. Memory forensics is the process of analyzing volatile memory (RAM) to uncover evidence of malicious activities and understand a system’s state during execution. In traditional OS-level forensics, tools like Volatility and Rekall have proven effective in detecting hidden processes, injected code, and system anomalies. However, these tools do not operate at the firmware level, where threats can persist and operate undetected by OS-level defenses.
UEFI operates at a much lower level of the system, just above hardware, with high-privilege access to all system components. This gives attackers the ability to maintain persistence even across OS reinstalls and disk formatting. UEFI threats, such as function pointer hooking or malicious image loading, manipulate the boot process itself, which cannot be detected by traditional OS-level security measures. Moreover, certain UEFI components, like the Driver Execution Environment (DXE), load critical system drivers and protocols that are often targeted by attackers for hooking malicious code.
UEFI Memory Forensics Framework
To address the lack of forensic tools for analyzing UEFI runtime memory, we introduce a comprehensive framework for UEFI memory forensics. This framework consists of two main components:
-
UefiMemDump: A memory acquisition tool specifically designed to capture volatile UEFI memory during the runtime phase before OS initialization. UefiMemDump is implemented as both a DXE driver and a UEFI shell application. It enables the capture of complete system memory snapshots during UEFI execution, providing an essential tool for memory analysis in pre-OS environments.
-
UEFIDumpAnalysis: A suite of analysis modules designed to analyze the acquired UEFI memory dumps. These modules can detect various forms of UEFI-based attacks, including:
- Function Pointer Hooking Detection: Identifies unauthorized modifications to function pointers in service tables, a common technique for malware to hijack control flow.
- Inline Hooking Detection: Discovers code-level execution redirections that allow attackers to alter the flow of execution within UEFI services.
- UEFI Image Carving: Extracts and analyzes UEFI images from memory dumps, enabling the detection of malicious firmware or bootloaders.
The framework is designed to be extendable, allowing researchers and security practitioners to develop additional modules to detect emerging UEFI threats. This open-source toolset enhances the ability to investigate firmware-level threats and perform in-depth security analyses of the pre-OS phase.
Use Case and Proof-of-Concept
We demonstrate the effectiveness of the UEFI memory forensics framework through a series of tests against modern UEFI threats. The framework successfully detects attacks like ThunderStrike, CosmicStrand, and Glupteba bootkits, which use advanced techniques such as function hooking and image loading to persist in UEFI and subvert security mechanisms. By using our framework, security professionals can analyze memory from the UEFI phase, even when attackers have tampered with the boot process.
Our proof-of-concept implementation shows that the framework can identify key characteristics of malicious UEFI behavior, making it an essential tool for detecting firmware-level malware that may evade traditional security measures.
Contributions of this Work
-
Introduction of UEFI Memory Forensics: This is the first framework dedicated to analyzing UEFI memory during the pre-OS phase. By addressing the gap in existing tools, our work opens new avenues for deep security analysis and the detection of firmware-level threats.
-
Comprehensive Analysis Modules: We provide a set of analysis modules capable of detecting common malicious techniques like function pointer hooking and inline hooking, which are often used by UEFI bootkits to gain control over the boot process.
-
Open-Source Contribution: Our framework is open-source, allowing the research community and cybersecurity practitioners to further develop and refine the tool, fostering collaborative efforts to strengthen UEFI security.
-
Effective Threat Detection: Our framework successfully identifies modern UEFI threats, demonstrating its potential to detect sophisticated bootkits and provide greater visibility into the firmware layer of systems.
Conclusion and Future Work
The introduction of a dedicated UEFI memory forensics framework marks a significant step forward in understanding and mitigating firmware-level threats. By providing the tools to capture and analyze UEFI runtime memory, we give researchers and security professionals the ability to detect sophisticated attacks that target the boot process and persist across reboots.
Future work can focus on improving the scalability of the framework to handle larger systems and incorporating real-time detection capabilities for live environments. Additionally, as UEFI security threats continue to evolve, continuous updates and new analysis modules will be essential to keeping up with emerging attack techniques.
By making this tool open-source, we invite further collaboration in the field of below-OS security, helping to create a more secure and resilient computing environment.As UEFI security becomes an increasingly critical aspect of overall system defense, how do you think memory forensics tools at the firmware level will evolve to address emerging threats in the coming years?
What's Your Reaction?