Few Edges Are Enough: Using Graph Neural Networks for Network Attack Detection with Few-Shot Learning
The increasing sophistication of cyberattacks highlights the need for robust cybersecurity defenses, especially as digital infrastructures become more complex. The integration of Machine Learning (ML) and Deep Learning (DL) techniques in detecting cyberattacks is one of the most promising solutions to enhance security.
Graph Neural Networks (GNNs), in particular, have gained traction due to their ability to model the interconnected nature of network data, where nodes represent hosts and edges represent the flows between them. However, most GNN-based models for network attack detection rely heavily on labeled data, which can be difficult and expensive to obtain in real-world scenarios.
To address this issue, researchers have turned to unsupervised and self-supervised learning (SSL) approaches, which eliminate the need for large labeled datasets. While these methods are good at identifying anomalies, they struggle with distinguishing true attacks from benign anomalies. In this paper, we introduce Few Edges Are Enough (FEAE), a GNN-based architecture trained with SSL and Few-Shot Learning (FSL), which allows for effective attack detection with only a minimal number of labeled examples.
Challenges in Attack Detection
The primary challenge in network attack detection is the imbalance between labeled attack data and benign network traffic. Traditional GNN-based models are trained on large, labeled datasets that include a variety of attack scenarios. However, obtaining such datasets in real-world environments is challenging due to privacy concerns and the sheer volume of traffic data. Without labeled attack data, models tend to overfit to benign traffic patterns, leading to high false positive rates when trying to identify actual attacks.
Unsupervised and self-supervised techniques, although useful in detecting anomalies, still suffer from the problem of false positives. For example, a first-time SSH connection between two hosts might be flagged as suspicious due to the lack of prior labeled data, even if it’s a legitimate connection. Hence, a solution is needed that can effectively leverage the small amount of labeled attack data while maintaining high detection accuracy.
Introducing FEAE
FEAE is a novel approach that utilizes a hybrid self-supervised objective combined with few-shot learning (FSL) to distinguish between benign and malicious network activity. The key idea behind FEAE is to leverage minimal labeled data (i.e., just one malicious event for each attack type) and combine it with SSL methods to improve attack detection accuracy.
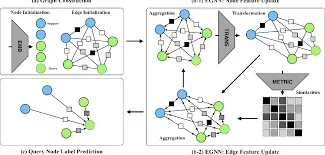
FEAE operates on network flow data, which is converted into a graph representation where nodes represent hosts (e.g., IP addresses) and edges represent network flows. These graph-based representations are enriched with additional features, such as packet count and mean packet size, to better capture the behavior of the network.
The architecture of FEAE consists of three main components:
-
GNN Encoder: This module computes node and edge embeddings by capturing the relationships between hosts through graph topology and network flow features. It uses the self-supervised learning module for training.
-
SSL Module: The SSL module employs both contrastive and reconstruction-based objectives. The contrastive objective differentiates between positive and augmented negative edges, while the reconstruction objective, combined with few-shot examples, creates embeddings that separate malicious from benign edges.
-
Few-Shot Decoder: This decoder uses a supervised learning approach to classify the edges based on the learned embeddings. It specifically focuses on classifying malicious attack edges using the few-shot labels available.
Key Contributions
-
First GNN-based FSL Approach for Network Attack Detection: FEAE is the first approach to apply Few-Shot Learning within the context of network attack detection using GNNs, where most similar approaches rely on supervised or unsupervised techniques.
-
Few-Shot Aware Reconstruction Loss: FEAE integrates few-shot malicious samples within the self-supervised training loop. This allows the model to group similar attack families in the embedding space, making it easier to distinguish them from benign network activities.
-
Reduction in Labeling Effort: The most significant contribution is the finding that only one malicious edge per attack type is enough to approach or even surpass the performance of fully-supervised methods. This dramatically reduces the need for extensive labeled datasets in practical scenarios.
Experimental Setup and Results
In the experiments, FEAE was compared to several supervised and unsupervised methods on two well-known network datasets. The results show that FEAE not only outperforms self-supervised GNN baselines but also surpasses some supervised approaches in terms of detection accuracy. By using as few as one labeled malicious event for each attack type, FEAE achieves competitive results that would typically require much larger datasets.
Conclusion
FEAE offers a novel and practical solution to the problem of network attack detection, reducing the dependency on extensive labeled datasets. By leveraging the power of Few-Shot Learning and Self-Supervised Learning, FEAE can detect attacks with a minimal amount of labeled data, making it suitable for real-world scenarios where labeled data is scarce. The hybrid objective used in the training process allows FEAE to not only detect anomalies but also classify them into meaningful attack categories. Future work can expand on this framework by incorporating more attack families and exploring ways to optimize the few-shot learning process further.
Future Directions
-
Incorporating Dynamic Network Topologies: Future work could explore how FEAE can handle dynamic or changing network topologies to improve its robustness.
-
Scalability: While FEAE performs well on current datasets, its scalability to larger network environments with millions of nodes and edges is an area for further exploration.
-
Real-time Detection: Integrating FEAE into real-time detection systems would require further optimization to ensure low-latency performance while maintaining high accuracy.
What's Your Reaction?