Investigating Oblivious Transfer over Noisy Multiple Access Channels
Oblivious Transfer (OT) is a fundamental cryptographic primitive that plays a crucial role in secure multiparty computation (SMC). It involves two senders and a receiver, where the sender provides two messages and the receiver selects one while keeping the unchosen message hidden.
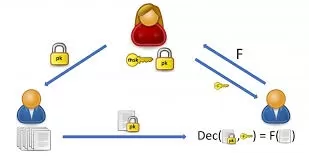
In the world of cryptography, Oblivious Transfer (OT) is a key building block that ensures secure communication between parties. Its relevance spans across numerous applications, particularly in the realm of secure multi-party computations (MPC), where privacy and confidentiality are paramount. At its core, OT enables a sender to transmit multiple messages to a receiver while keeping the unchosen messages hidden from them, all while ensuring the sender remains unaware of which message was selected. However, the performance of OT in noisy communication environments—specifically over a Multiple Access Channel (MAC)—has remained relatively underexplored. This blog post delves into a recent study that pushes the boundaries of OT, investigating its viability over noisy MACs with two senders and a receiver, and tackling the challenges of both honest-but-curious and malicious parties.
Understanding the Core Concepts
Before diving into the research, let's quickly break down some of the key terms.
-
Oblivious Transfer (OT): OT is a cryptographic protocol where a sender (Alice) has several messages, and a receiver (Bob) chooses one message to receive, while the sender does not know which message was chosen. This ensures that the receiver's choice remains private and the sender is oblivious to it. The classic 1-out-of-2 OT protocol allows Alice to send two messages, and Bob can choose one, with the other remaining hidden from him.
-
Multiple Access Channel (MAC): In communication theory, a MAC is a model where multiple senders share the same communication channel to transmit messages to a single receiver. In OT, this translates to multiple senders (non-colluding) sending independent messages to a common receiver.
-
Honest-but-Curious vs. Malicious: An honest-but-curious party follows the protocol but may try to learn more than they are entitled to, while a malicious party actively tries to break the protocol and manipulate the system to their advantage.
The Challenge Addressed by the Research
While OT has been extensively studied in ideal (noiseless) communication settings, the introduction of noise in a MAC model introduces several complexities:
-
Noisy Communication: Noise interferes with the transmission of messages, making it harder for the receiver to correctly decode messages. This problem is exacerbated when multiple senders are involved, as it becomes difficult to ensure privacy and integrity across the noisy channel.
-
Honest-but-Curious Parties: In a scenario where the parties involved are honest but curious, the challenge lies in designing protocols that prevent additional information leakage beyond what is intended by the protocol.
-
Malicious Receiver: A more complex scenario arises when the receiver is malicious. In this case, the receiver could try to gain information about the unchosen message, thus undermining the security of the communication.
A New Approach: The Authors' Contribution
This research presents a multiparty protocol designed to handle OT over a noisy MAC, where two non-colluding senders communicate with one receiver. The study introduces several innovations to address the challenges posed by noisy channels and the potential for malicious behavior:
-
Honest-but-Curious Protocol: The authors propose reducing the MAC model to a simplified correlation that maintains the security guarantees necessary for OT. By focusing on specific correlations, the protocol ensures that parties cannot extract unauthorized information.
-
Malicious Receiver Scenario: For scenarios where the receiver is malicious, the study introduces a mechanism that defines achievable rate regions for OT. This mechanism ensures that the malicious receiver cannot learn more than the information they are entitled to, thus maintaining the integrity of the communication.
-
Rate Region Bounds: The study provides upper and lower bounds on the OT capacity for noisy MACs, shedding light on the achievable OT rates in real-world noisy communication channels.
Implications for the Field
The implications of this work are significant for secure communication in multi-party systems. The study presents new protocols and theoretical bounds that can be used to improve the efficiency and security of OT in noisy communication environments. Some potential applications include:
-
Secure Multi-Party Computations: The results can be used to improve the security of multi-party computations in real-world settings, where communication channels are often noisy and imperfect.
-
Privacy-Preserving Cryptographic Protocols: OT forms the foundation for several cryptographic protocols that ensure privacy, such as secure auctions and private information retrieval. Enhancing OT over noisy channels could improve these applications' robustness.
-
Telecommunication and Networking: This research opens up new avenues for designing secure communication protocols in noisy networks, which is crucial for areas like encrypted messaging and secure data sharing.
Conclusion: A Step Forward in Secure Communication
This research provides a fresh perspective on the problem of Oblivious Transfer over noisy Multiple Access Channels, offering innovative solutions to address both noise and the potential for malicious actors. By introducing new protocols and deriving bounds on OT capacity, the study paves the way for more secure and efficient communication in real-world scenarios.
The next step in this research will likely involve refining these bounds and exploring practical implementations in modern communication systems, from secure cloud computing to encrypted messaging services.
As communication channels continue to evolve, research like this is vital to ensure that privacy and security remain at the forefront of technological advancements.
What are your thoughts on the future of OT in noisy communication environments? How might this research impact real-world secure communication applications?
What's Your Reaction?