Understanding Hacking: Types and Methods...!!!
Understanding the types and methods of hacking is essential for protecting individuals and organizations from cyber threats. By staying informed about the latest hacking techniques and implementing robust security measures, people and businesses can better defend against these threats.

Introduction
Hacking involves the unauthorized access or manipulation of computer systems, networks, or data. It can be driven by various motives, including financial gain, espionage, or simply the challenge. Understanding the different types and methods of hacking is crucial for safeguarding individuals and organizations from cyber threats. This article provides an overview of the most common types of hacking and the techniques hackers use.
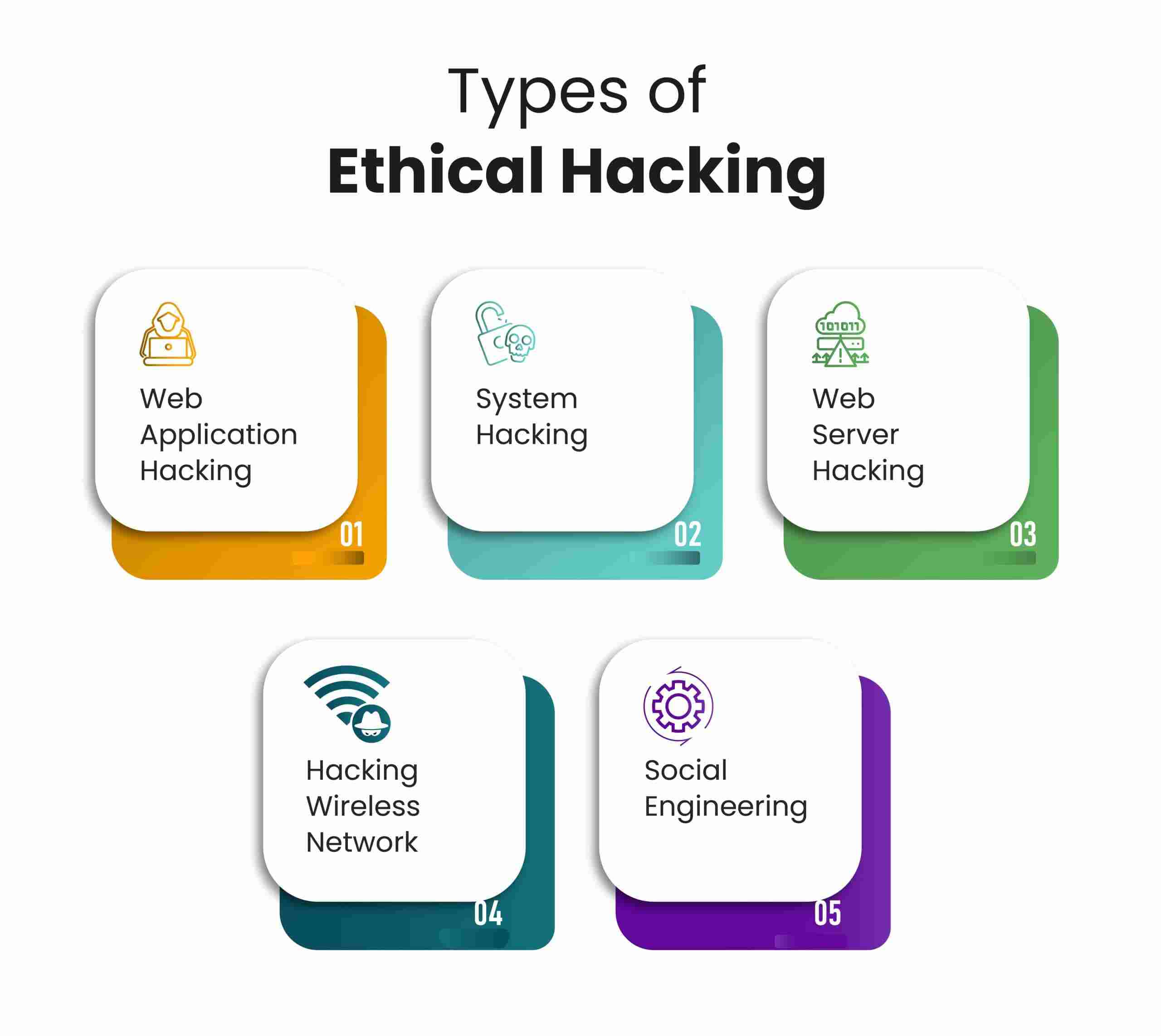
Types of Hacking
-
Phishing: Phishing is a form of social engineering attack where hackers use deceptive emails or messages to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or personal details. These emails often appear to come from legitimate sources, such as banks or reputable companies.
-
SQL Injection: SQL injection is a technique used to exploit vulnerabilities in a database application's software. Hackers insert malicious SQL code into a query, enabling them to access, modify, or delete data in the database.
-
Cross-Site Scripting (XSS): XSS attacks occur when hackers inject malicious scripts into web pages viewed by other users. These scripts can steal information, such as cookies or session tokens, and send it to the attacker.
-
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: DoS attacks overwhelm a system, network, or service with traffic, causing it to slow down or crash. DDoS attacks are similar but involve multiple compromised systems (botnets) targeting a single system.
-
Password Attacks: Password attacks involve attempting to guess or crack passwords to gain unauthorized access to systems or accounts. Common methods include brute force attacks, dictionary attacks, and credential stuffing.
-
Man-in-the-Middle (MITM) Attacks: In MITM attacks, hackers intercept and manipulate communication between two parties without their knowledge. This can be used to steal information or inject malicious content into the communication.
-
Malware Attacks: Malware is malicious software designed to damage or disrupt systems. Common types of malware include viruses, worms, trojans, ransomware, and spyware.
-
Zero-Day Exploits: Zero-day exploits target vulnerabilities in software that are unknown to the vendor. Hackers take advantage of these vulnerabilities before they can be patched, making them particularly dangerous.
-
Advanced Persistent Threats (APTs): APTs are prolonged and targeted cyberattacks where hackers gain access to a network and remain undetected for an extended period. These attacks are often aimed at stealing sensitive information or espionage.
-
Social Engineering: Social engineering involves manipulating individuals into divulging confidential information or performing actions that compromise security. This can include phishing, pretexting, baiting, and tailgating.

Methods of Hacking
-
Exploiting Software Vulnerabilities: Hackers often look for weaknesses in software applications, operating systems, or firmware. By exploiting these vulnerabilities, they can gain unauthorized access or control over systems.
-
Network Intrusions: Hackers can gain access to networks through various methods, such as exploiting weak passwords, using malware, or taking advantage of unpatched software.
-
Credential Stuffing: Credential stuffing involves using stolen usernames and passwords from one breach to try to access accounts on other platforms. This method relies on the fact that many people reuse passwords across multiple sites.
-
Email Attachments and Links: Hackers often use email attachments or links to deliver malware or direct users to phishing websites. These emails can appear to come from trusted sources, making them more convincing.
-
Public Wi-Fi Networks: Public Wi-Fi networks are often unsecured, making them prime targets for hackers. By intercepting data transmitted over these networks, hackers can steal sensitive information.
-
Physical Access: Gaining physical access to a device or network can provide hackers with direct access to sensitive information. This can be done through theft, social engineering, or exploiting physical security weaknesses.
-
Social Media: Hackers can use social media platforms to gather information about individuals or organizations, which can be used in targeted attacks. This can include personal details, job roles, or network connections.
-
Mobile Devices: Mobile devices are increasingly targeted by hackers due to their widespread use and the sensitive information they contain. This can include contact information, financial data, and location data.
-
Cloud Services: As more organizations move to the cloud, hackers are targeting cloud services to gain access to sensitive data. This can involve exploiting vulnerabilities in cloud infrastructure or using stolen credentials to access cloud accounts.
-
Internet of Things (IoT) Devices: IoT devices, such as smart home appliances and wearables, are often less secure than traditional computing devices. Hackers can exploit these vulnerabilities to gain access to networks and steal data.
Understanding the types and methods of hacking is essential for protecting individuals and organizations from cyber threats. By staying informed about the latest hacking techniques and implementing robust security measures, people and businesses can better defend against these threats. Regularly updating software, using strong passwords, and being cautious of suspicious emails and links are just a few steps that can help mitigate the risk of hacking.
What's Your Reaction?

















